IPsec Packet by Packet
Phase-1 of IPSEC
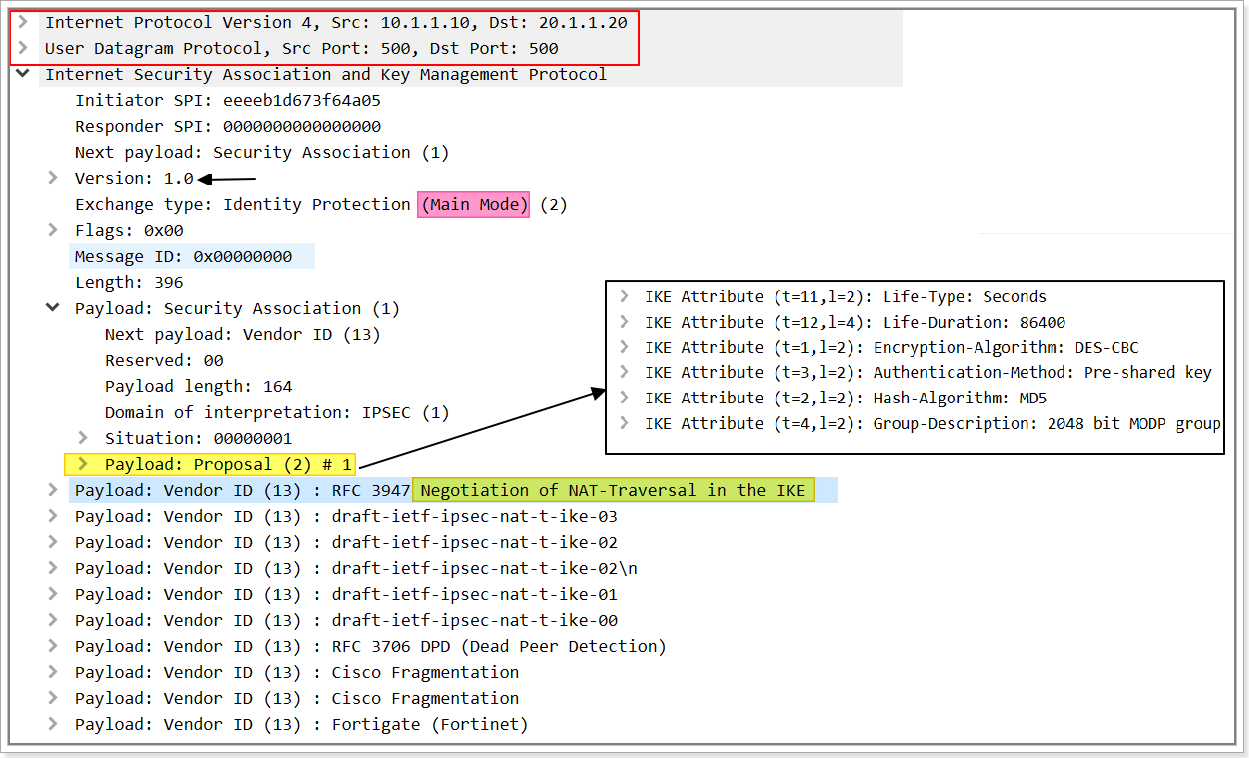
In 1st two message it negotiate proposal and IKE version and NAT-T capability
Proposal/transform >>
HAGLE - HASH, AUTH, DH Group, Lifetime ,Encryption
1st Message IPSec main mode:
SA Payload
Proposal payload
Trasform payload
SPI/cookie
2nd IPsec Main mode message
3rd Message IPSec main mode:
In 3rd and 4th message, it will do key exchange and Nonce and NAT-D (IP & Port hash)
DH key exchange ::
DH algo used to agree on same shared secret and generate key material
DH public value is calculated (public value is mathematical calculation of private keys)
-->>It generate public and private key's
--->>It share public key's (x^b)
(x^b)==>g^a mod p (MOD(generator of private key=a))
g^ab=>(x^b)^a mod p (large prime no)
==>Each side has their public key and nonce (Ni_b is the Initiator's Nonce, and Nr_B is the Responder's Nonce)
==>It generate SKEYID = prf(pre-shared-key, Ni_b | Nr_b)
The Seed value is then combined with the DH Shared Secret (and a few other values) to create three Session Keys:
1>>a Derevative key
SKEYID_d = prf(SKEYID, g^ab | CKY-I | CKY-R | 0)
SKEYID_d (d for derivative): not used by Phase 1.
-->Phase2 --->[It is used as seed key for Phase2 keys, i.e. seed key for production traffic keys in Plain English]
g^ab -->Shared secret in DH process
2>>Authentication key
SKEYID_a = prf(SKEYID, SKEYID_d | g^ab | CKY-I | CKY-R | 1)
(a for authentication)
This key is used to protect message integrity in every subsequent packets as soon as both peers are authenticated (peers will authenticate each other in next 2 packets). Yes, I know, we verify the integrity by using a hash but throwing a key into a hash adds stronger security to hash and it's called HMAC.
HMAC=>keyed hash message authentication code (HMAC) is a specific type of message authentication code (MAC) involving a cryptographic hash function[pre-shared +SKEYID_a +hash}
3>>an Encryption key.
SKEYID_e = prf(SKEYID, SKEYID_a | g^ab | CKY-I | CKY-R | 2)
SKEYID_e (e for encryption): you'll see that the next 2 packets are also encrypted.
As selected encryption algorithm for this phase was AES-CBC (128-bits) then we use AES with this key to symmetrically encrypt further data.
Next packet:
1. Hash of pre-shared key
2. Identification
ike 0:VPN:3: dec D3701B9BC03E3E03FA02FBC561FE57
ike 0:VPN:3: peer identifier IPV4_ADDR 20.1.1.20
ike 0:VPN:3: PSK authentication succeeded
ike 0:VPN:3: authentication OK
ike 0:VPN:3: established IKE SA d3701b9bc03e3e03/fa02fbc561fe5763
6th Message of main mode:
5th and 6th Message in short












Comments
Post a Comment