IPsec Main and Quick Mode packet flow (Decrypted)
Main Mode 1st Message:
Generation of the initiator cookie — An 8-byte pseudo-random number used for anticlogging CKY-I = md5{(src_ip, dest_ip), random number, time, and date}
Generation of the responder cookie — An 8-byte pseudo-random number used for anticlogging CKY-R = md5{(src_ip, dest_ip), random number, time, and date}
Main Mode 2nd Message:
Before 3rd and 4th message:
- Public key: Xa ,Xb
- Nonce = Ni, Nr
How public key is created?
- DH public value = Xa
- Xa = g^a mod p
- g is the generator
- p is a large prime number
- a is a private secret known only to the initiator
Main Mode 3rd message:
- Key exchange
- Public key
- NAT-D
Before 5th and 6th message:
Initiator secret = (Xb)a mod p = (Xa)b mod p = responder secret
This value is the shared secret between the two parties and is also equal to g^ab
PRF => Pseudo random function based on negotiated hash
- SKEYID's = PRF [Pre-shared key, Ni ,Nr ]
- SKEYID_d = PRF [SKEYID, g^ab | CKY-I | CKI-R| 0 ] ==> To calculate key material
- SKEYID_a = PRF [SKEYID, SKEYID_d, g^ab | CKEY-I | CKI-R | 1 ] ==> Data Integrity and Authentication to subsequent message
- SKEYID_e = PRF [SKEYID, SKEYID_a, g^ab | CKEY-I | CKI-R | 2 ] ==> Encrypt subsequent message
Main Mode 5th Message:
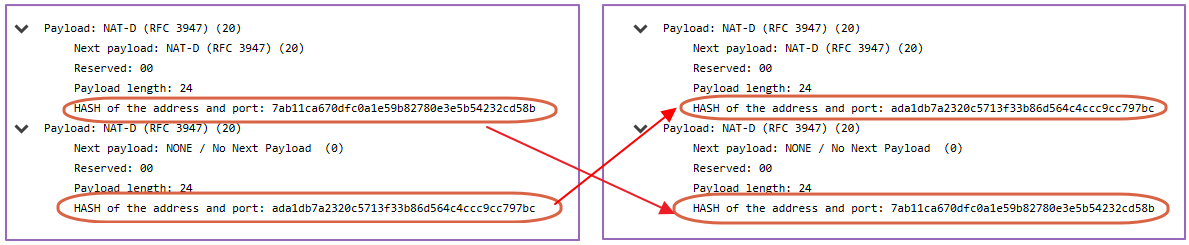
Main Mode 6th Message:
If PFS (Perfect forward secrecy) is enabled, it will created new DH secret
- New Nonce Generated: Nr'
- New DH public value = Xb'
- Xb' = g^b mod p
- g is the generator
- p is a large prime number
- b is a private secret known only to the responder
Quick Mode 2nd Message:
Initiator generates IPsec keying material ==>
Step 1. Generate new DH shared secret = (Xb')a mod p
Step 2. IPsec session key for incoming IPsec SA
= PRF (SKEYID_d, protocol (ISAKMP), new DH shared secret, SPIr, Ni', Nr')
Step 3. IPsec session key for outgoing IPsec SA
= PRF (SKEYID_d, protocol (ISAKMP), new DH shared secret, SPIi, Ni', Nr')
Responder generates IPsec keying material ==>
Step 1. Generate new DH shared secret = (Xa')b mod p
Step 2. IPsec session key for incoming IPsec SA
= PRF (SKEYID_d, protocol (ISAKMP), new DH shared secret, SPIi, Ni', Nr')
Step 3. IPsec session key for outgoing IPsec SA
= PRF (SKEYID_d, protocol (ISAKMP), new DH shared secret, SPIr, Ni', Nr')


















Comments
Post a Comment