How to create bulk addresses and address-group in Fortigate
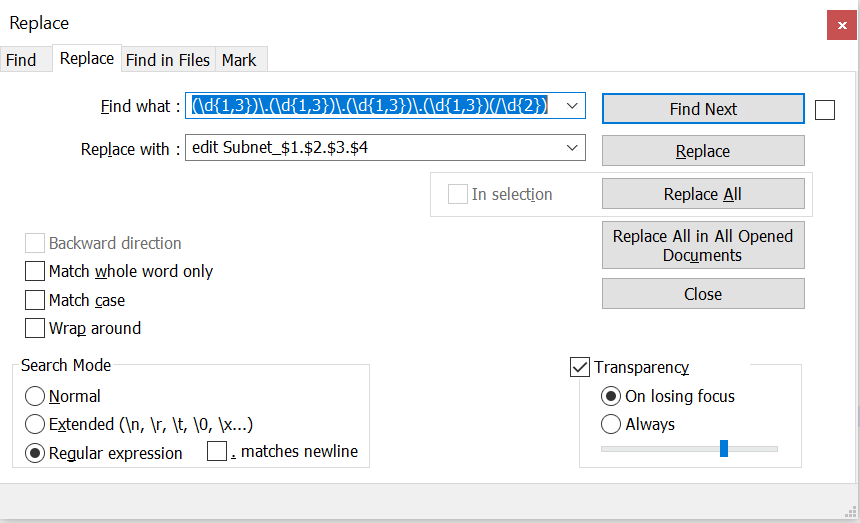
Recently I came accross a scenario where I need to create bulk addresses in fortigate and call those in firewall policy. Use below script add flow procedure to create address =================================== A}To create address_objects ------------------------------------ 1))Open notepad > use 10.132.4.0/24 10.234.0.0/16 172.17.11.0/24 192.168.20.0/27 2)) Use find & replace (ctrl +H) in notepad and replace following string find:: (\d{1,3})\.(\d{1,3})\.(\d{1,3})\.(\d{1,3})(/\d{2}) Replace:: edit Subnet_$1.$2.$3.$4\nset subnet $1.$2.$3.$4$5\nnext\n Note: Search mode should be selected as "regular expresssion" 3))Add below line after changes config firewall address B}To create address_grp ------------------------------- 1))Open notepad > use 10.132.4.0/24 10.234.0.0/16 172.17.11.0/24 192.168.20.0/27 2))Create member in row find:: (\d{1,3})\.(\d{1,3})\.(\d{1,3})\.(\d{1,3})(/\d{2}) Replace:: "Subnet_$1.$2....




